How to Integrate Data Destruction Techniques into Your Cyber Security Approach
Wiki Article
Checking Out the Relevance of Information Destruction in the Context of Computer System Protection Services and Protecting Confidential Information
In a period where information violations are progressively typical, the significance of reliable information destruction can not be overstated. Organizations needs to adopt rigorous steps to guarantee that delicate info is not only secured throughout its lifecycle but likewise decisively gotten rid of when no more necessary. The approaches used for data removal, combined with conformity to legal requirements, play an essential duty in keeping confidentiality and trust. The implications of these techniques extend beyond mere conformity, affecting a company's reputation and operational integrity in the digital industry. What strategies can organizations carry out to enhance their information destruction procedures?Understanding Data Damage
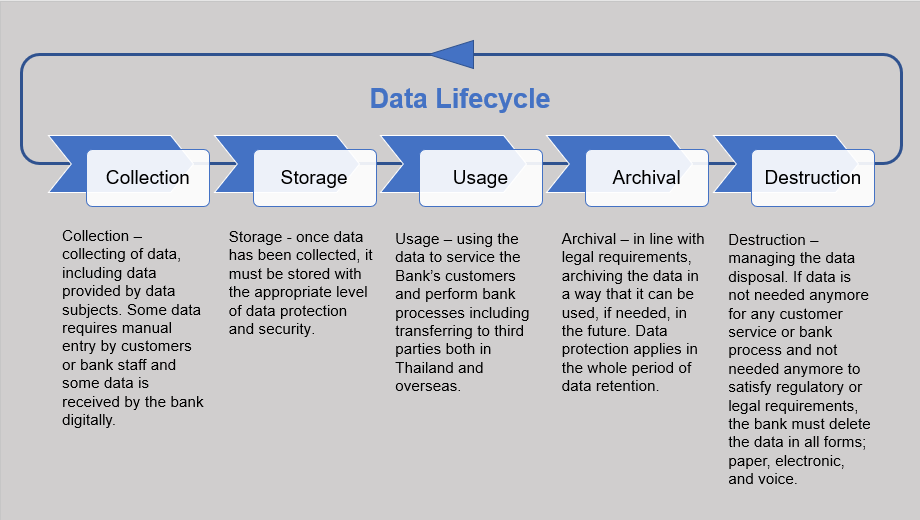
Data devastation is a vital element of computer protection that involves the permanent elimination of information from storage space tools to avoid unauthorized accessibility and potential data violations. In an increasingly electronic landscape, companies deal with enhanced threats associated with delicate info being improperly accessed or manipulated. Reliable data devastation safeguards versus these dangers, making sure that personal dataâEUR" such as consumer information, copyright, and financial recordsâEUR" can not be recuperated after disposal.Comprehending the value of data damage prolongs beyond plain conformity with governing and lawful structures; it is necessary for maintaining business stability and trust. When data is improperly managed or improperly damaged, the repercussions can be severe, consisting of monetary loss, reputational damages, and lawful obligations.

Approaches of Data Obliteration
One prevalent approach is information cleaning, which involves overwriting existing information with random patterns multiple times. This method makes the initial data irretrievable, making it a popular choice for companies seeking to secure private information.
An additional technique is degaussing, which utilizes an effective magnetic field to interrupt the magnetic domain names on storage space tools, properly getting rid of the data. This strategy is particularly efficient for magnetic media however is not appropriate to solid-state drives.
Physical devastation is one more durable technique, squashing or entailing the shredding of storage tools. This technique warranties that information recuperation is essentially impossible, making it optimal for very delicate info.
Finally, encryption can serve as a corresponding method to information elimination. By securing data before removal, companies can add an added layer of security, making sure that also if residues are recovered, they remain hard to reach without the decryption key. Each approach must be chosen based upon the degree of information level of sensitivity and the certain safety and security demands of the company.
Legal Conformity and Information Security
Organizations should navigate a complicated landscape of lawful needs connected to data safety, specifically after carrying out techniques of information obliteration. Various laws, such as the General Information Defense Policy (GDPR) and the Wellness Insurance Coverage Mobility and Liability Act (HIPAA), enforce rigorous standards on exactly how organizations need to take care of and dispose of sensitive data. Failure to comply with these laws can cause significant lawful repercussions, including significant penalties and reputational damages.Data damage processes have to be carefully recorded to show compliance with suitable laws and standards. This paperwork not only acts as evidence of adherence to legal responsibilities however resource additionally highlights a commitment to safeguarding sensitive info. Organizations ought to also develop clear plans regarding information retention useful content and destruction timelines, guaranteeing that information is not held longer than essential.

Moreover, regular audits and evaluations of information devastation methods are important to keep conformity and adjust to advancing lawful structures (data destruction). By proactively addressing lawful requirements, companies can mitigate dangers related to information violations and demonstrate their dedication to data safety and security. Inevitably, focusing on legal conformity in data destruction procedures is not just a governing obligation, but a fundamental facet of a robust information safety approach
Influence on Company Credibility
The online reputation of a company can be substantially impacted by its approach to data damage and administration. In today's electronic landscape, where data violations can happen at any minute, the failure to appropriately throw away sensitive info can cause extreme repercussions. Organizations that improperly take care of data devastation danger subjecting private customer details, which not just goes against privacy laws however also wears down trust amongst customers and stakeholders.A damaged online reputation can lead to lowered client loyalty, as customers come to be hesitant to involve with a service that has demonstrated carelessness in securing their information. Furthermore, unfavorable promotion surrounding an information violation can have a long-term result, as prospective customers might be discouraged by the regarded absence of protection. This can cause a direct decrease in income and market share.
Furthermore, businesses that click over here now prioritize data destruction as part of their protection strategy can enhance their online reputation by showcasing their dedication to guarding sensitive info. By embracing rigorous information administration techniques, companies can not only alleviate threats however also position themselves as credible entities in their respective industries, therefore reinforcing their total brand name image.
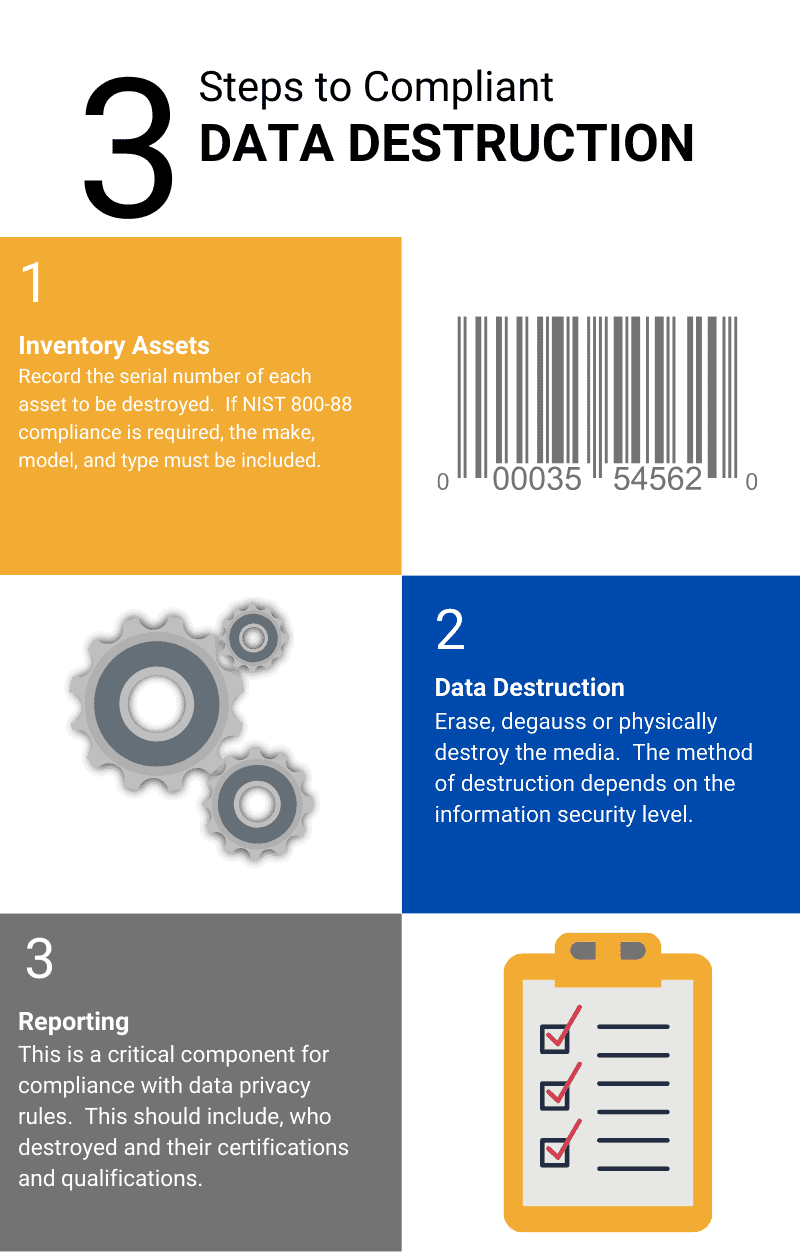
Ideal Practices for Secure Disposal
Applying ideal methods for secure disposal of data is important for minimizing threats connected with data breaches and ensuring compliance with personal privacy regulations. Organizations should embrace an extensive data disposal plan that lays out treatments for both physical and digital data damage.For physical information storage gadgets, such as disk drives, shredding or degaussing is recommended to stop data recovery. Furthermore, companies need to keep a chain of wardship documentation throughout the disposal procedure, making sure liability and traceability of disposed things.
For electronic information, making use of software that adheres to sector standards for information cleaning is vital. This software application should overwrite existing data several times, making recuperation essentially impossible. It is also essential to verify the efficiency of the information damage process via audits or third-party assessments.
Educating staff members on safe and secure disposal techniques includes an additional layer of safety, as human mistake can frequently lead to information exposure. Consistently evaluating and upgrading disposal plans makes sure alignment with advancing policies and technical advancements. By implementing these ideal techniques, companies can dramatically lower the danger of unapproved information access and improve their total data protection approach.
Conclusion
In conclusion, data destruction is a fundamental element of computer system security services that ensures the protection of secret information from unauthorized accessibility. Executing efficient approaches of data obliteration, adhering to legal compliance, and acknowledging the influence on company credibility are essential parts of a thorough data safety approach. By adopting ideal methods for protected disposal, organizations can cultivate trust fund with customers and secure sensitive data, eventually contributing to a more safe digital landscape.In an era where data violations are increasingly common, the relevance of reliable data destruction can not be overstated.Information damage is an important part of computer system protection that involves the permanent removal of information from storage tools to protect against unauthorized access and potential data breaches. Organizations ought to also establish clear policies regarding information retention and devastation timelines, making sure that information is not held longer than essential.
By proactively attending to lawful requirements, companies can mitigate risks linked with information breaches and show their dedication to information security (data destruction). Eventually, prioritizing lawful conformity in information devastation procedures is not simply a governing responsibility, yet a fundamental facet of a durable data protection method
Report this wiki page